Table of Contents
Picture an armory of weapons left loaded and unattended. They aren’t being watched, they aren’t being maintained, and no one intends to use them – but every one of them is ready to go off the moment someone picks them up. That’s what unused secrets represent in modern infrastructure: live credentials sitting like loaded guns, one careless moment or malicious hand away from pulling the trigger and starting the fire.
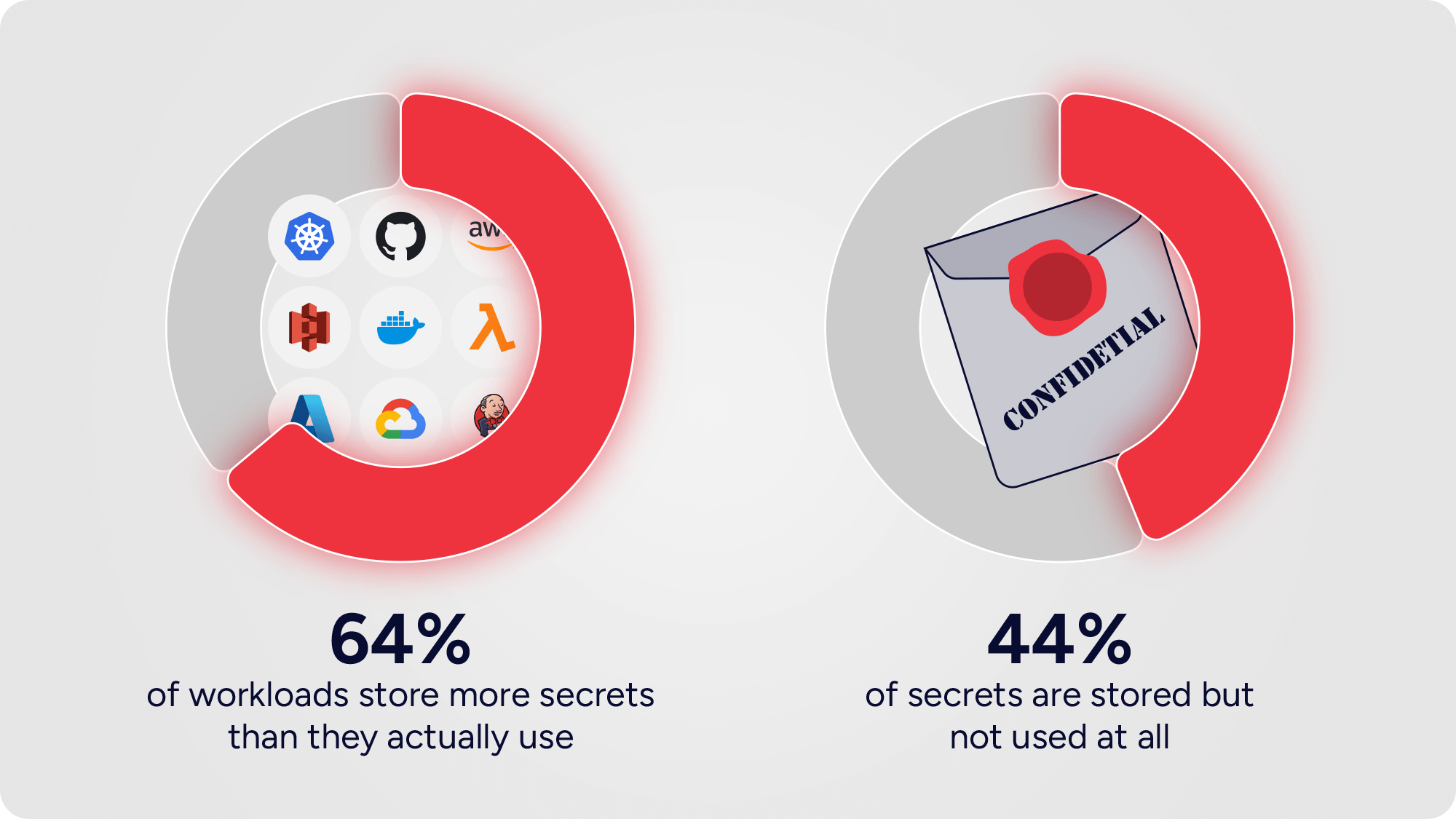
Our latest analysis reveals:
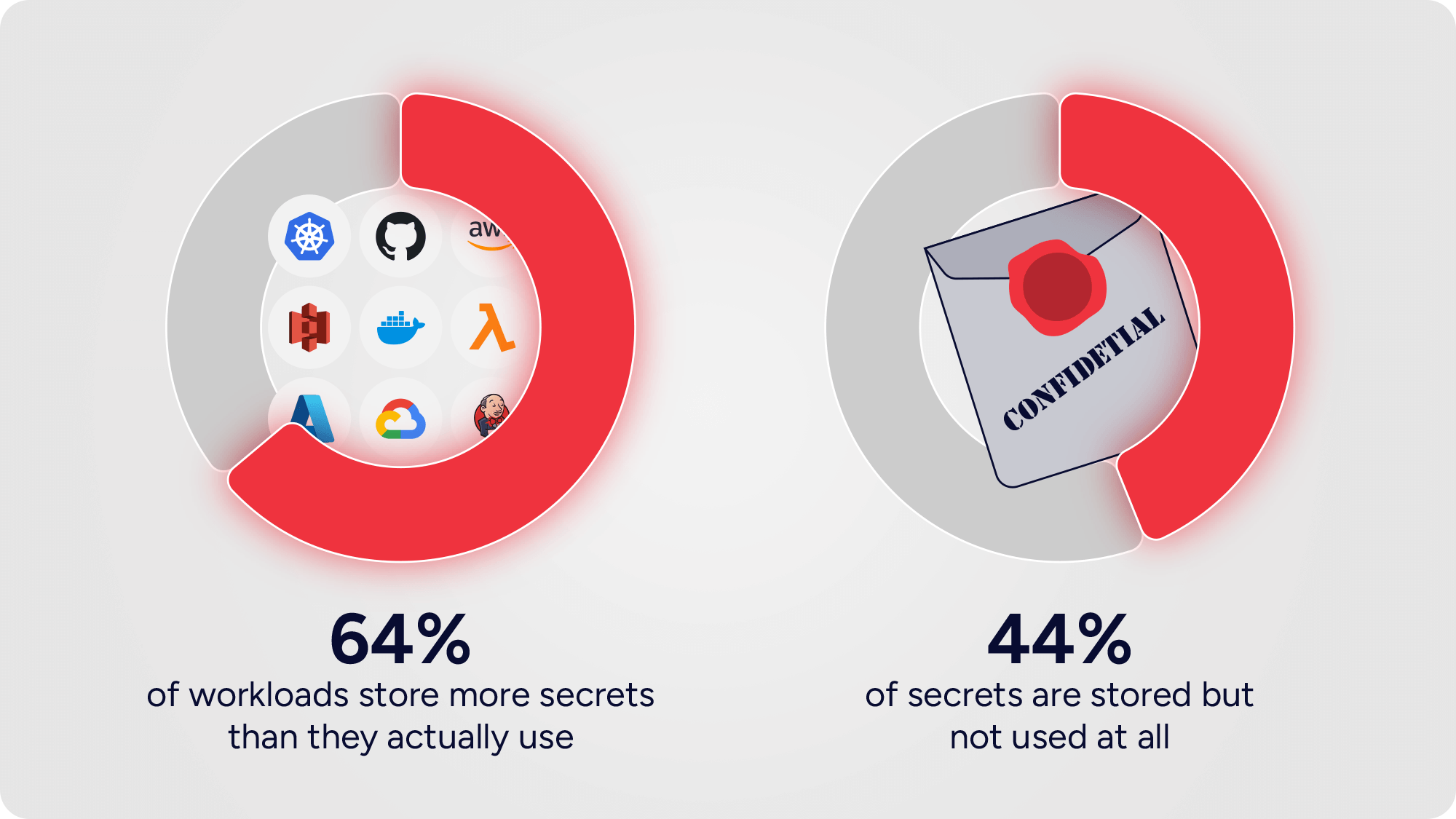
These aren’t harmless leftovers. They’re live rounds scattered across your environment. Each one expands the attack surface, each one drains resources, and each one invites the possibility of a breach.
Where Secrets Hide
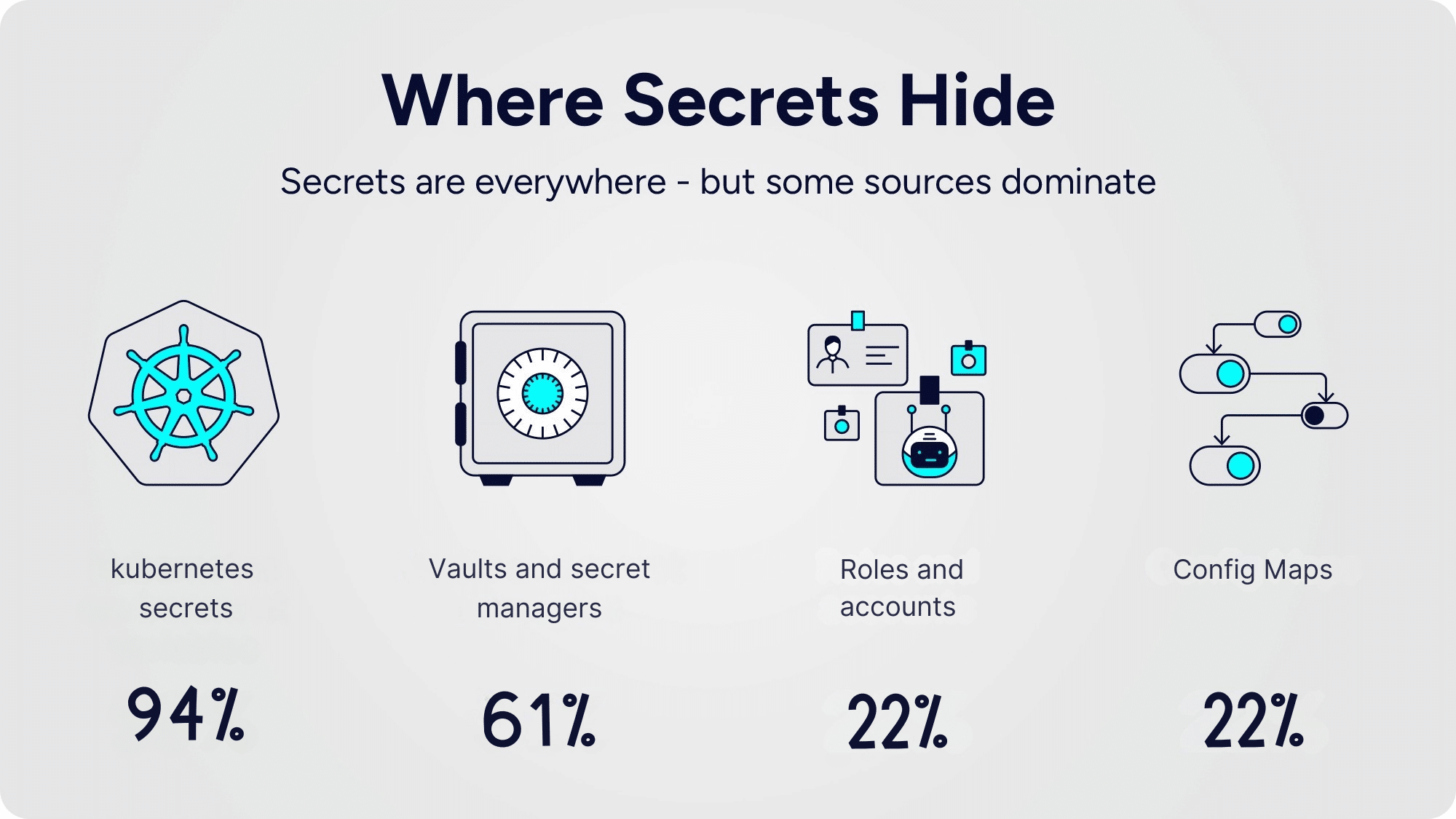
The data shows Kubernetes sits at the center of the problem. Workloads overwhelmingly lean on environment variables, while vaults and secret managers are layered on top. Instead of solving the problem, this combination multiplies it: more systems, more secrets, more risk.
*The numbers do not complete to 100% since there is duplication between the sources
The Hidden Cost of Unused Secrets
Unused and over-provisioned secrets don’t just sit idle – they actively create risk:
- Expanded attack surface: A single forgotten credential can enable lateral movement.
- Operational drag: Rotations, audits, and vault management consume precious cycles.
- Visibility gaps: Teams know where secrets are stored, but rarely which ones are truly needed.
- Compliance exposure: Audits become brittle when dormant secrets linger in the system.
- Operational cost: Every secret stored in a secret manager carries a direct financial cost, multiplying with sprawl.
Leaving secrets loaded but unused is like leaving weapons armed and unattended. It’s not a question of if they’ll be misused – it’s a matter of when.
Why Vaults Aren’t Enough
Vaults were designed to centralize storage, not solve usage. They give organizations a sense of control while secrets continue to multiply underneath. The problem isn’t where secrets live. The problem is that they exist at all.
As automation accelerates and workloads become more ephemeral, vault-based models simply cannot keep pace. Secret sprawl isn’t contained – it’s just relocated.
The Alternative: Secretless Access
At Hush, we believe the strongest protection is eliminating static secrets entirely. Our platform replaces them with dynamic, policy-driven access that delivers:
- Just-in-time, least-privilege access – nothing over-provisioned, nothing idle.
- No static secrets to steal, leak, or rotate.
- Real-time visibility into actual workload-to-service interactions.
- Adaptive IAM policies enforced at runtime, derived from observed behavior.
This isn’t incremental improvement. It’s a new foundation: secretless, identity-driven, and built for Zero Trust.
Closing the Gap
Secrets should enable, not endanger. Yet nearly half of them do nothing but weigh down security teams and expose organizations to risk.
With Hush, you can finally turn the page. Instead of managing more and more secrets, you can remove them from the equation altogether. The result: leaner, safer infrastructure where access is precise, dynamic, and invisible to attackers.
Because the only secure secret is the one that doesn’t exist.