Feb 24, 2026
•
Access Management
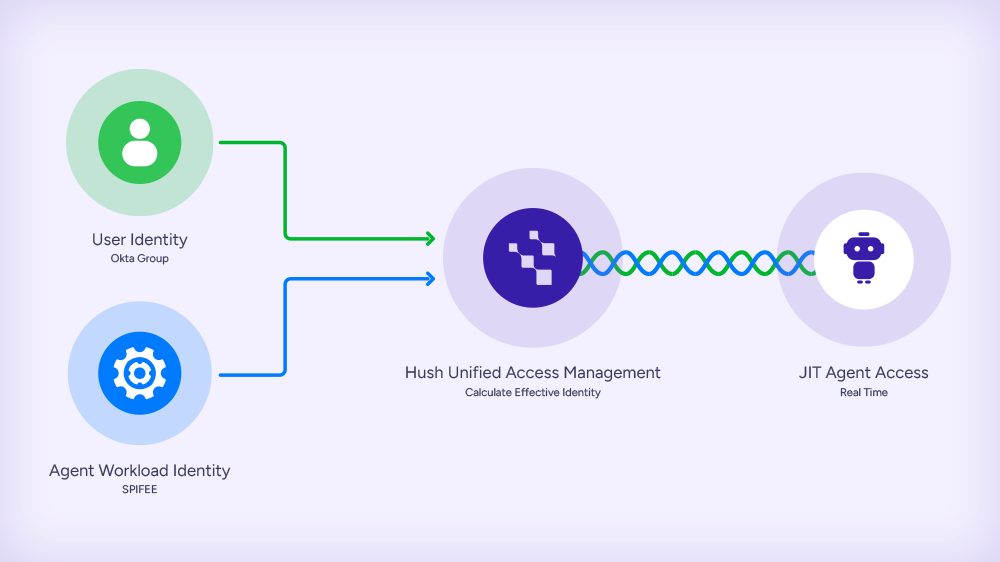
The Attack Surface Hasn’t Shrunk. It’s Shifted.
Feb 16, 2026
•
Identity Security
The NHI Security Illusion: Why Your Tools Detect Everything and Protect Nothing
Feb 9, 2026
•
Identity Security
AI Agents Are Getting Powerful. What’s Stopping Them from Exfiltrating Your Data?
Jan 19, 2026
•
Identity Security
Build Your Security for Assume Breach, Not for Good Hygiene
Dec 24, 2025
What Happens When You Add Identity to API Keys
Dec 3, 2025
•
Breaches
Shai-Hulud 2.0: Why Attackers Hunt Machine Identities
Nov 24, 2025
•
Identity Security
Why Storm the Castle When You Already Hold the Keys to the Kingdom?
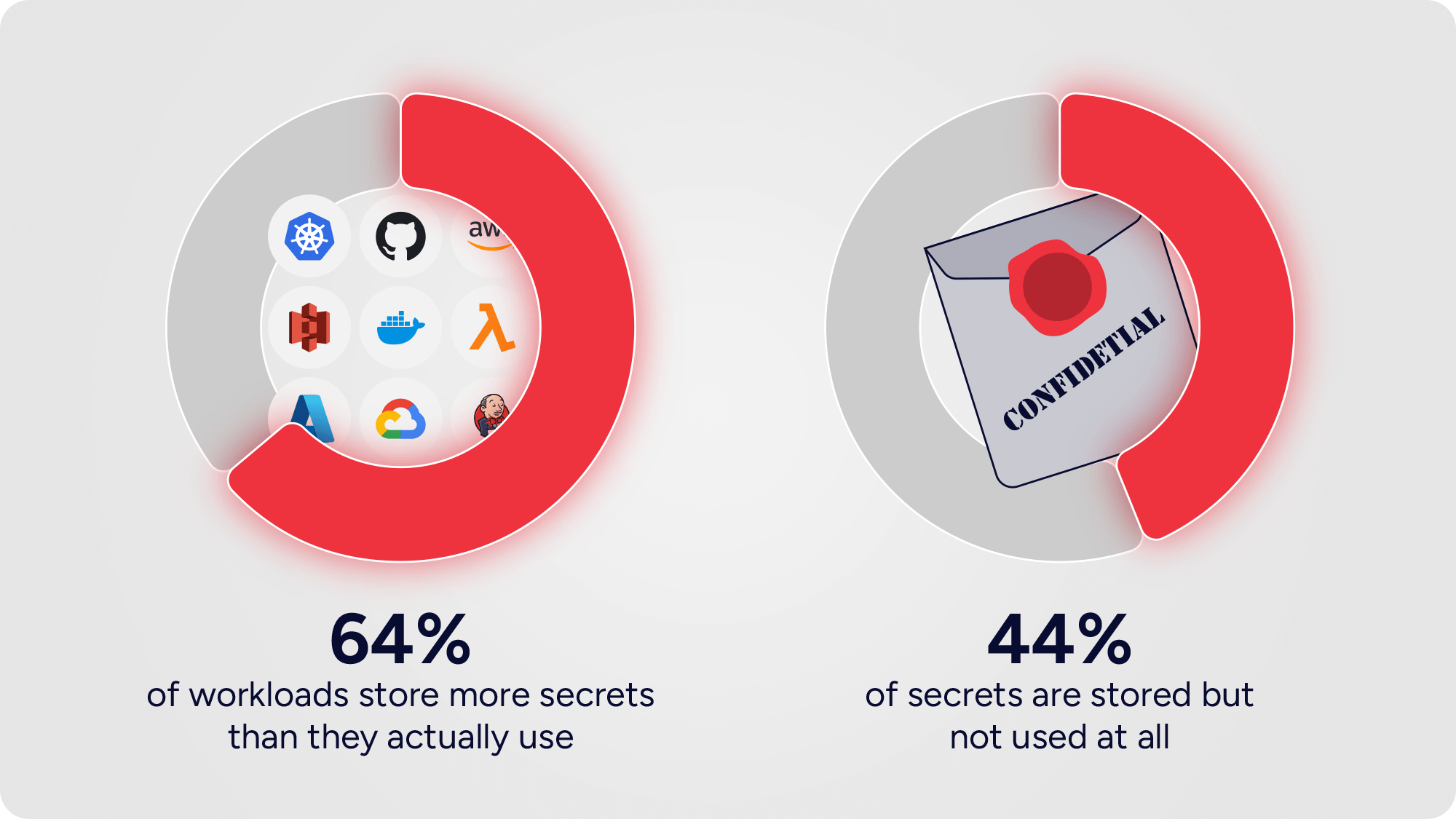
Oct 30, 2025
•
Research
Unused Secrets: The loaded guns in your infrastructure
Oct 20, 2025
Why Runtime Insight Is the Missing Piece in Certificate Management
Aug 17, 2025
•
Breaches