- View All
- Access Management
- Breaches
- Identity Security
- Research
What Happens When You Add Identity to API Keys API keys and static secrets power most systems today, but they don’t scale securely. Learn why identity-based authentication is replacing secrets in modern architectures.
When applications need to talk to each other, they face a fundamental challenge: how does one system prove it’s legitimate when accessing another? For decades, we’ve relied on secrets - passwords, keys, and tokens - to solve this problem. But as our infrastructure has grown more complex and distributed, these approaches have shown their limitations. […]
Shai-Hulud 2.0: Why Attackers Hunt Machine Identities
Shai-Hulud Proved It: Attackers Hunt NHIs First, Because That’s Where the Power is Shai-Hulud wasn’t loud for the sake of noise, it was a powerful, well-structured attack that understood the modern software ecosystem better than many defenders do. And it validated the clearest trend in 2025 security: attackers prioritize non-human identities (NHIs) over everything else. Shai-Hulud’s […]
Why Storm the Castle When You Already Hold the Keys to the Kingdom?
Attackers aren’t breaching platforms — they’re abusing trusted tokens and integrations. This post explains the NHI attack blueprint and how to harden, rotate, and govern machine identities.
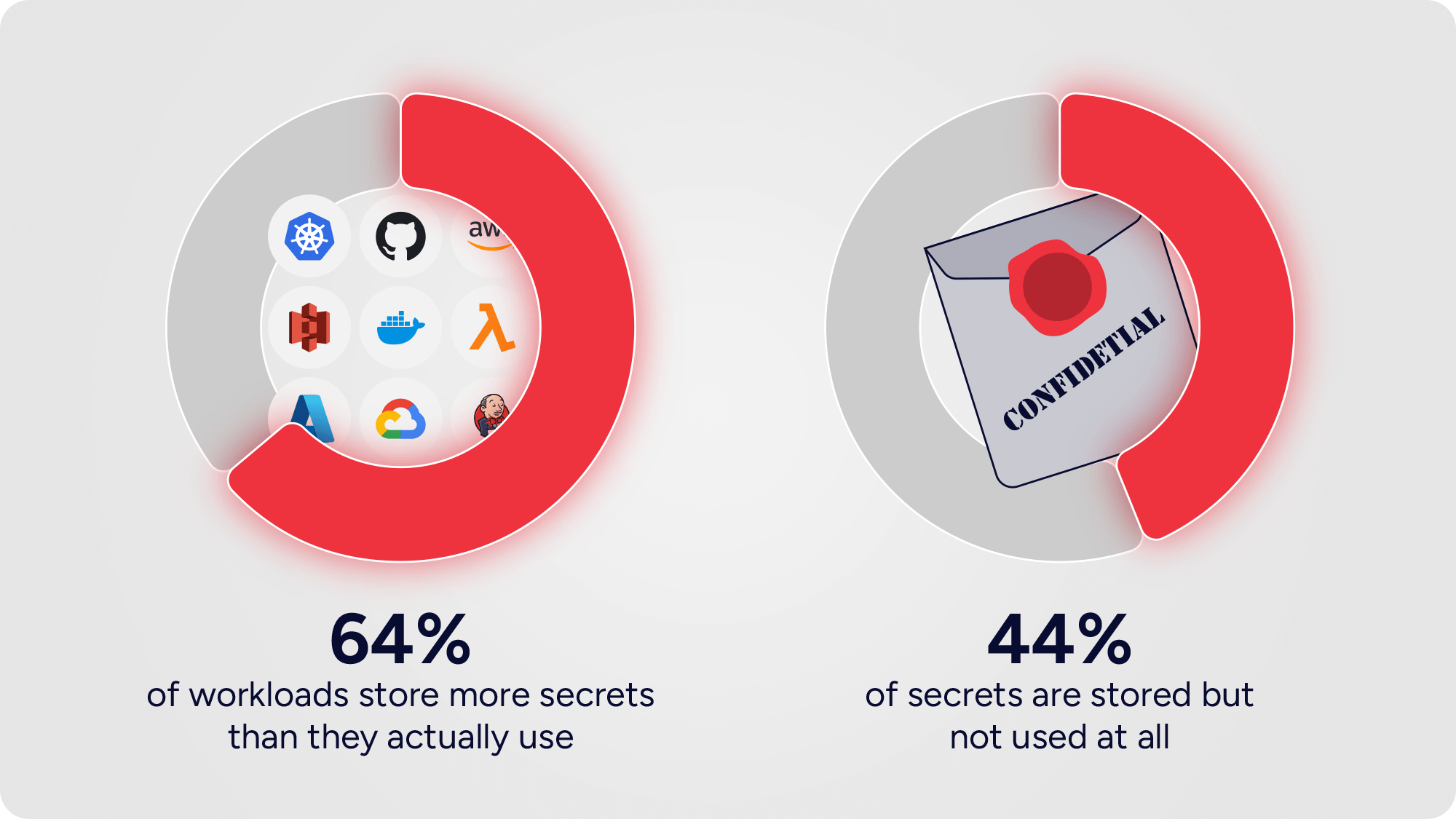
Unused Secrets: The loaded guns in your infrastructure
Most workloads are hoarding "loaded guns" in their infrastructure. Our analysis shows 43.74% of secrets are unused live credentials that expand your attack surface and drain resources. Vaults aren't the solution; eliminating secrets is. Discover the alternative: secretless access.
Why Runtime Insight Is the Missing Piece in Certificate Management
Machine identities are central to security, but certificate sprawl creates hidden risk. Move beyond static inventory to real-time visibility, control, and automated remediation for your machine identity landscape.
Vaults Are Done. This Train Has Left the Station.
Managing secrets is broken — risky, complex, and outdated. Hush Security offers a new approach: secretless, policy-driven access for every machine and AI agent, built for scale and simplicity.


