Mergers & Acquisitions Without the Chaos
Unify identities, secrets, and access without breaking production.
Integrate environments faster and more securely during M&A. Get visibility into what’s actually used, reduce duplicate and orphaned credentials, and apply consistent identity-based access and controls across both organizations with minimal disruption.
The Challenge
M&A creates instant identity and secrets chaos.
When two companies merge, you inherit:
- Multiple vaults and secret managers
- Duplicated service accounts, API keys, tokens, and certificates
- Inconsistent policies, ownership models, and access patterns
- Unknown dependencies across apps, pipelines, automation, and AI agents
The Solution
Scan First, Then Combine With Confidence
Hush starts by scanning the acquired environment to build a comprehensive, real-time view of all existing secrets and non-human identities. By combining static discovery with runtime telemetry, we identify what exists, what is actually used, and where the highest risks and dependencies are, before any consolidation begins.
Unified Inventory and Risk Prioritization
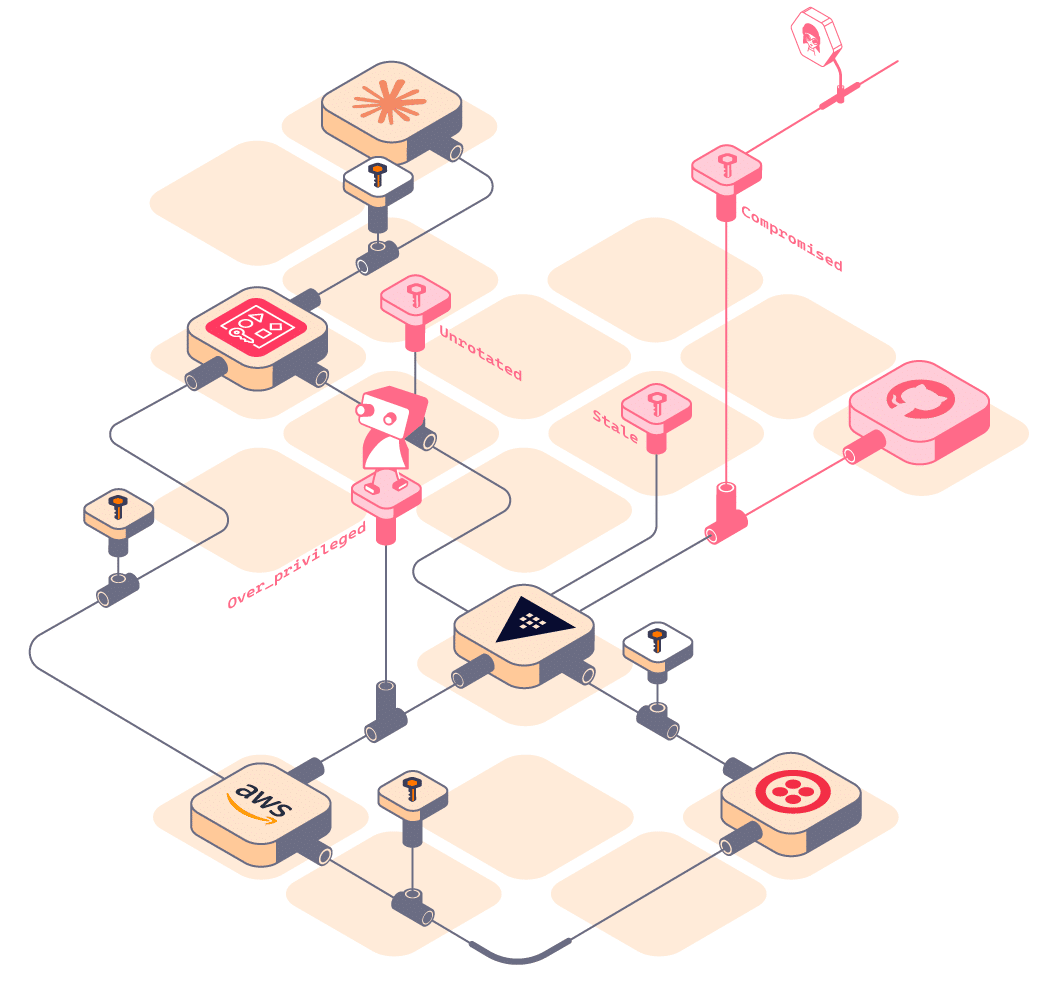
Because Hush correlates discovery with runtime usage, teams can quickly understand:
- Where each secret or NHI is used across services, workloads, and environments
- What depends on it right now across both organizations
- Whether it’s active, dormant, duplicated, orphaned, or risky
- Which credentials create the highest blast radius in the merged environment

Consolidate Without Breaking Production
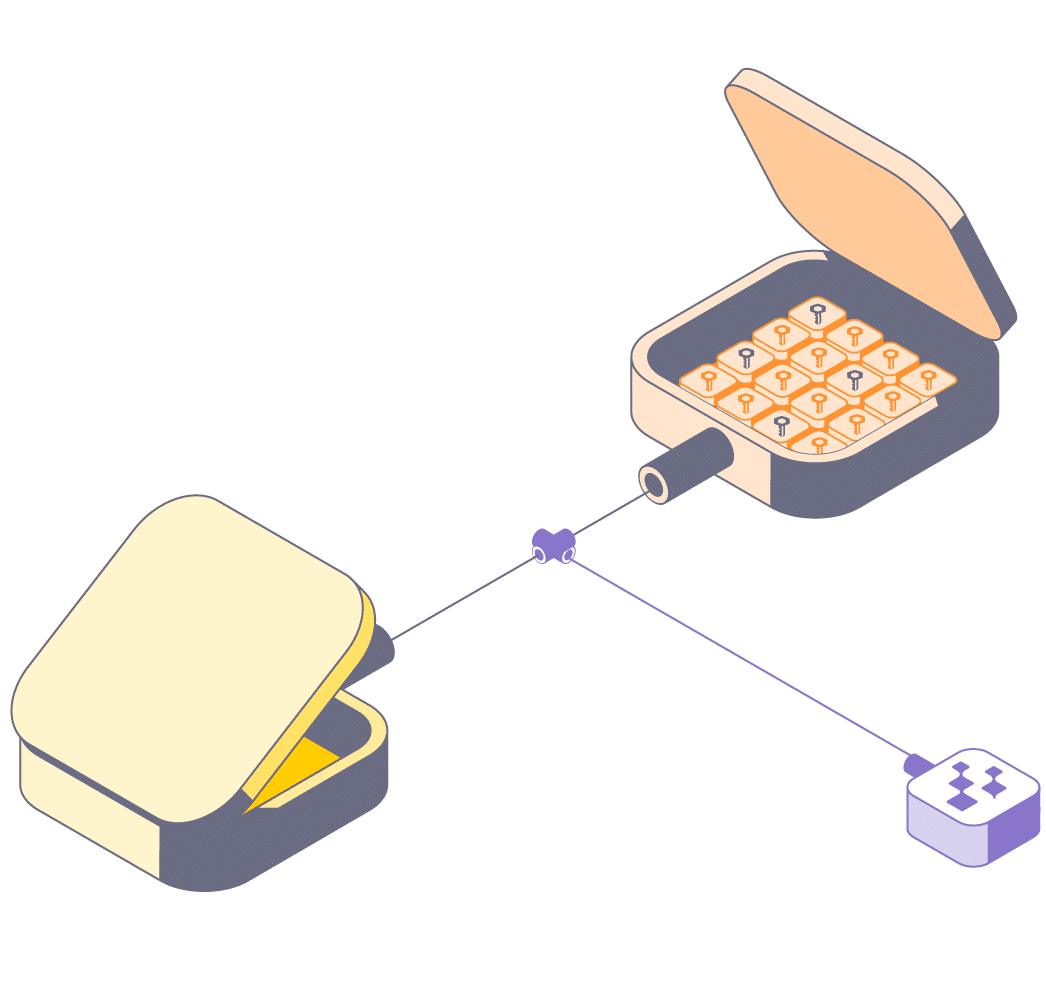
With complete coverage and live validation, M&A integration becomes faster and safer:
- Consolidate vaults and secret managers with confidence
- Reduce scope by skipping dead secrets and orphaned identities
- Identify duplicate credentials and eliminate unnecessary access paths
- Prevent outages by validating dependencies before changes go live

The Value
 Secure Integration
Accelerate secure integration across apps, infrastructure, and machine identities
Secure Integration
Accelerate secure integration across apps, infrastructure, and machine identities
 Usage-Based Risk
Reduce risk by identifying high-impact secrets and NHIs based on real usage
Usage-Based Risk
Reduce risk by identifying high-impact secrets and NHIs based on real usage
 Outage Prevention
Avoid production outages and broken workflows during consolidation
Outage Prevention
Avoid production outages and broken workflows during consolidation
 Attack Surface Reduction
Shrink attack surface by removing duplicates, orphans, and excessive privilege
Attack Surface Reduction
Shrink attack surface by removing duplicates, orphans, and excessive privilege
 Fast Time to Value
Achieve fast time to value with minimal integrations
Fast Time to Value
Achieve fast time to value with minimal integrations