Post-Quantum Certificate
Prepare for quantum. Prioritize rotations and upgrades.
Identify quantum-vulnerable certificates in real time, continuously assess cryptographic posture, and prioritize fixes based on what’s actually active across your machine identity ecosystem.
The Challenge
Quantum readiness is now a machine identity problem.
Modern environments rely on certificates for machine trust – across service meshes, Kubernetes, APIs, load balancers, SaaS, and internal services. But most organizations can’t answer basic PQC readiness questions with confidence:
- Which ones use weak algorithms, outdated protocols, or risky configurations?
- Where are these certificates used across service-to-service flows?
- What will break if we rotate, replace, or enforce stronger standards?
The Solution
Know What’s Active. Know What’s Quantum-Ready.
Hush continuously discovers certificates across your environments to build a real-time view of certificate usage and cryptographic posture. We assess each certificate to detect weak encryption, risky configurations, and lack of post-quantum readiness. When issues are identified, Hush automatically replaces and rotates certificates safely, so you strengthen security without manual effort or production risk.
Continuous PQC Posture Management
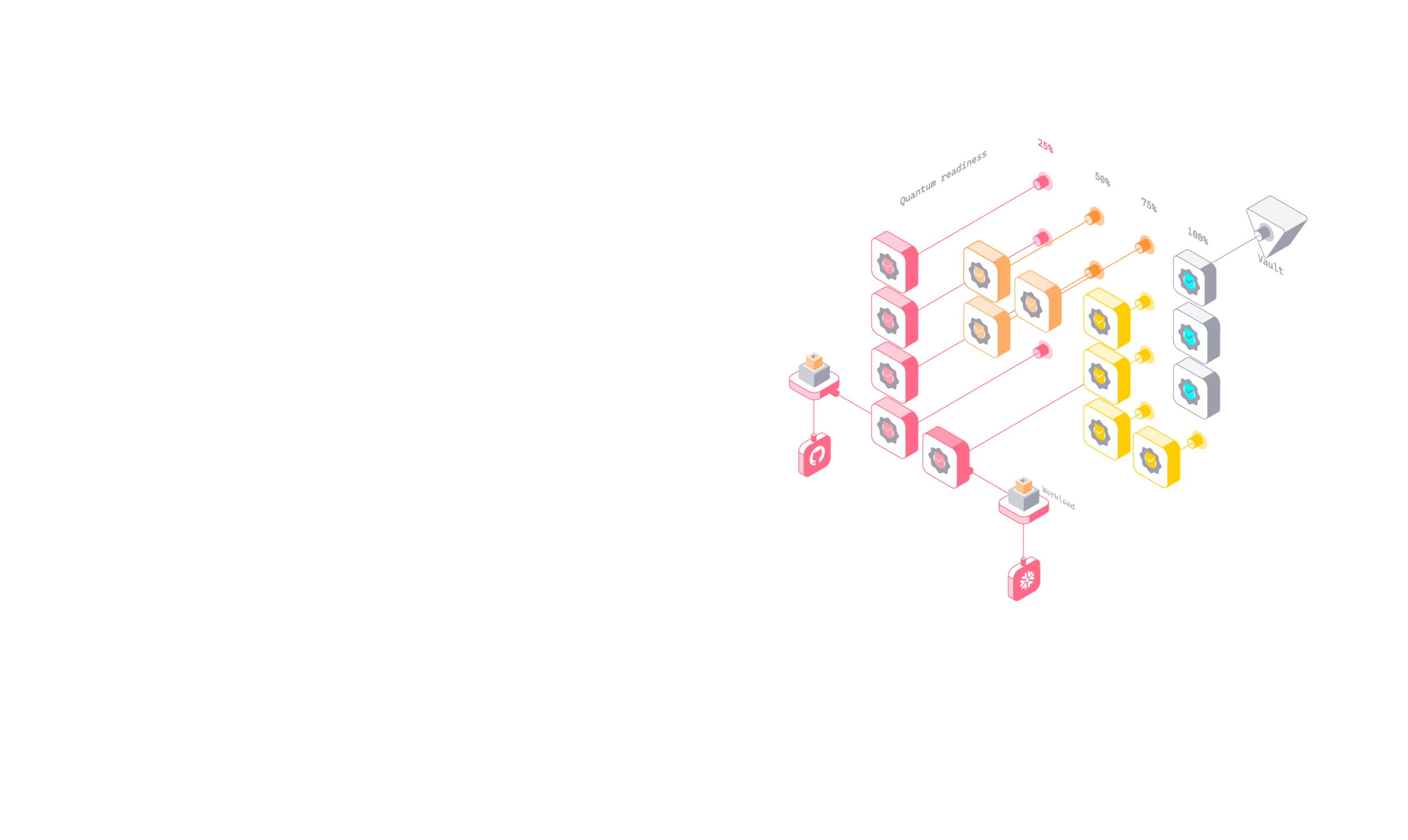
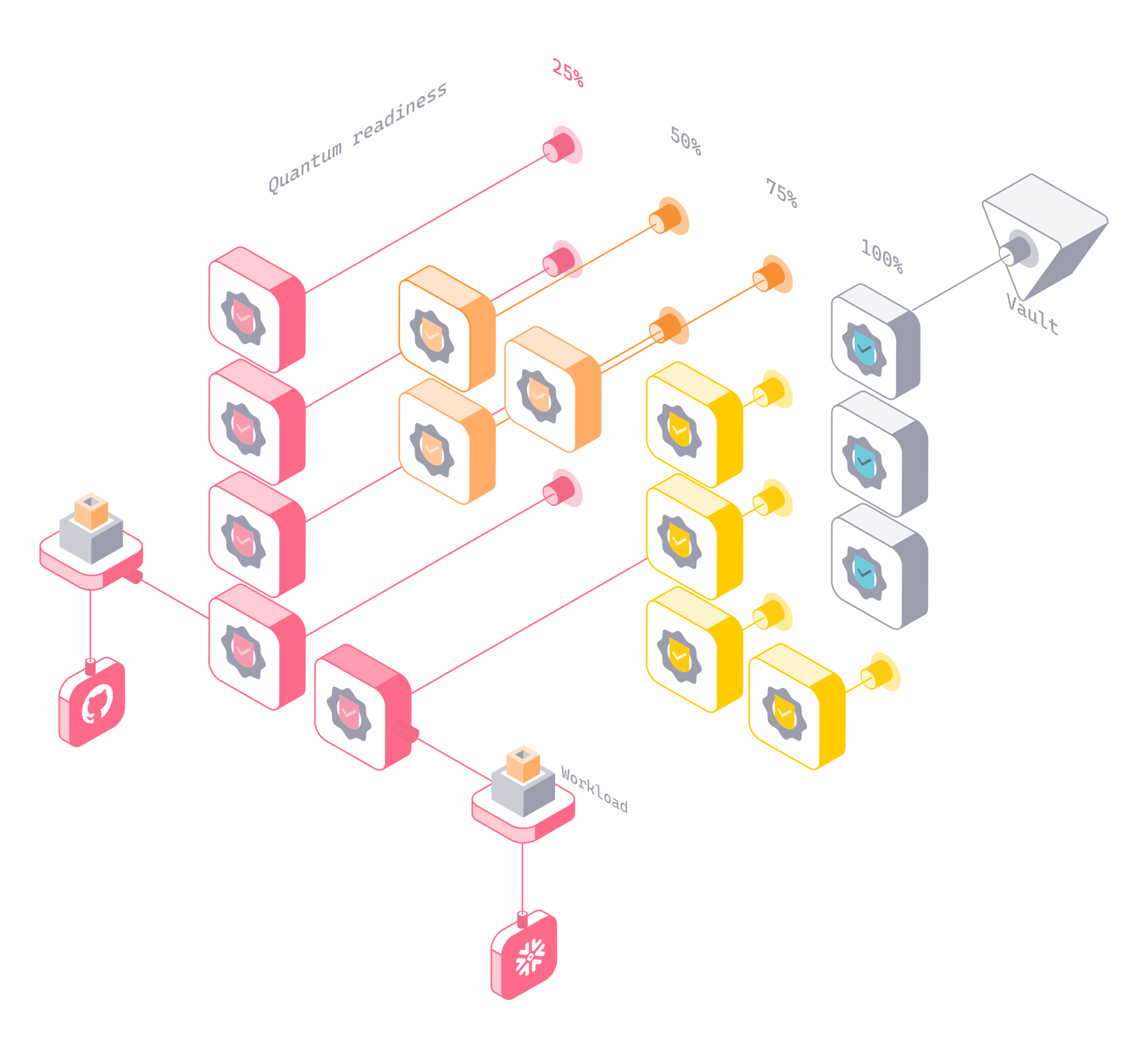
Continuously assess certificate cryptographic posture and quantum vulnerability across your enterprise.
- Assessment of encryption strength – flag weak algorithms, outdated protocols, and certificates lacking PQC readiness
- Runtime usage context – understand where certificates are actually used in live service-to-service and machine-to-machine flows
- Exposure mapping – see which workloads, services, and endpoints depend on each certificate
- Risk prioritization – surface certificates that matter most for quantum migration

Automated Remediation and Safe Hardening
Replace weak or non-PQC certificates with stronger, future-ready cryptography without breaking production.
- Policy-driven remediation – define organization-wide standards for cryptographic strength and PQC compliance
- Automated replacement and rotation – upgrade certificates as needed without manual intervention
- Reduced operational burden – eliminate spreadsheets, manual audits, and error-prone handoffs
- Continuous enforcement – maintain PQC posture as environments evolve and workloads spin up

The Value
 Operational Efficiency
Prioritize PQC readiness based on real runtime usage
Operational Efficiency
Prioritize PQC readiness based on real runtime usage
 Audit Readiness
Detect weak, expired, misconfigured, or non-compliant certificates
Audit Readiness
Detect weak, expired, misconfigured, or non-compliant certificates
 Outage Prevention
Prevent certificate-related outages
Outage Prevention
Prevent certificate-related outages
 Certificate Hygiene
Reduce cryptographic blind spots with continuous enterprise coverage
Certificate Hygiene
Reduce cryptographic blind spots with continuous enterprise coverage
 Fast Time to Value
Get fast time to value with lightweight deployment and minimal integrations
Fast Time to Value
Get fast time to value with lightweight deployment and minimal integrations