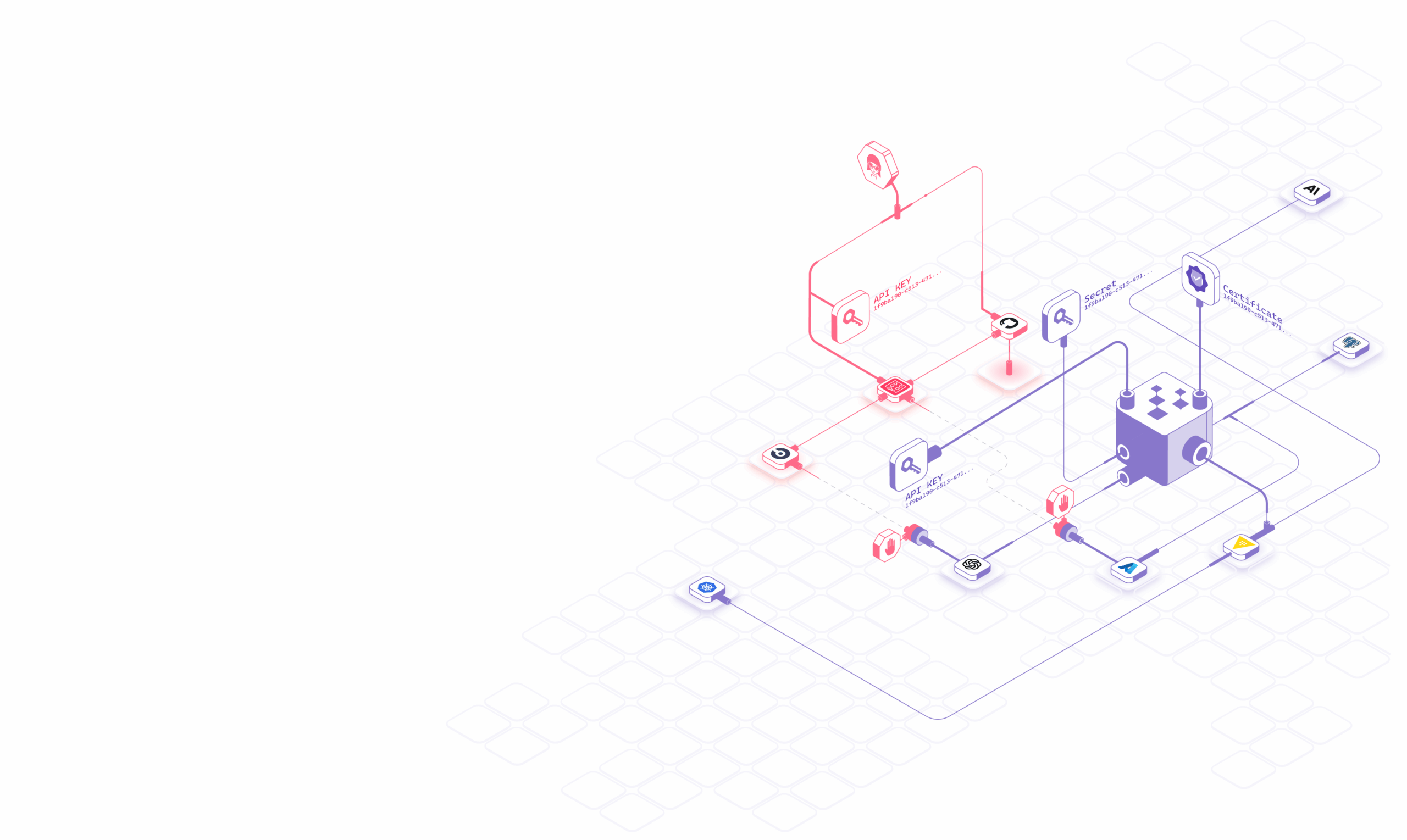
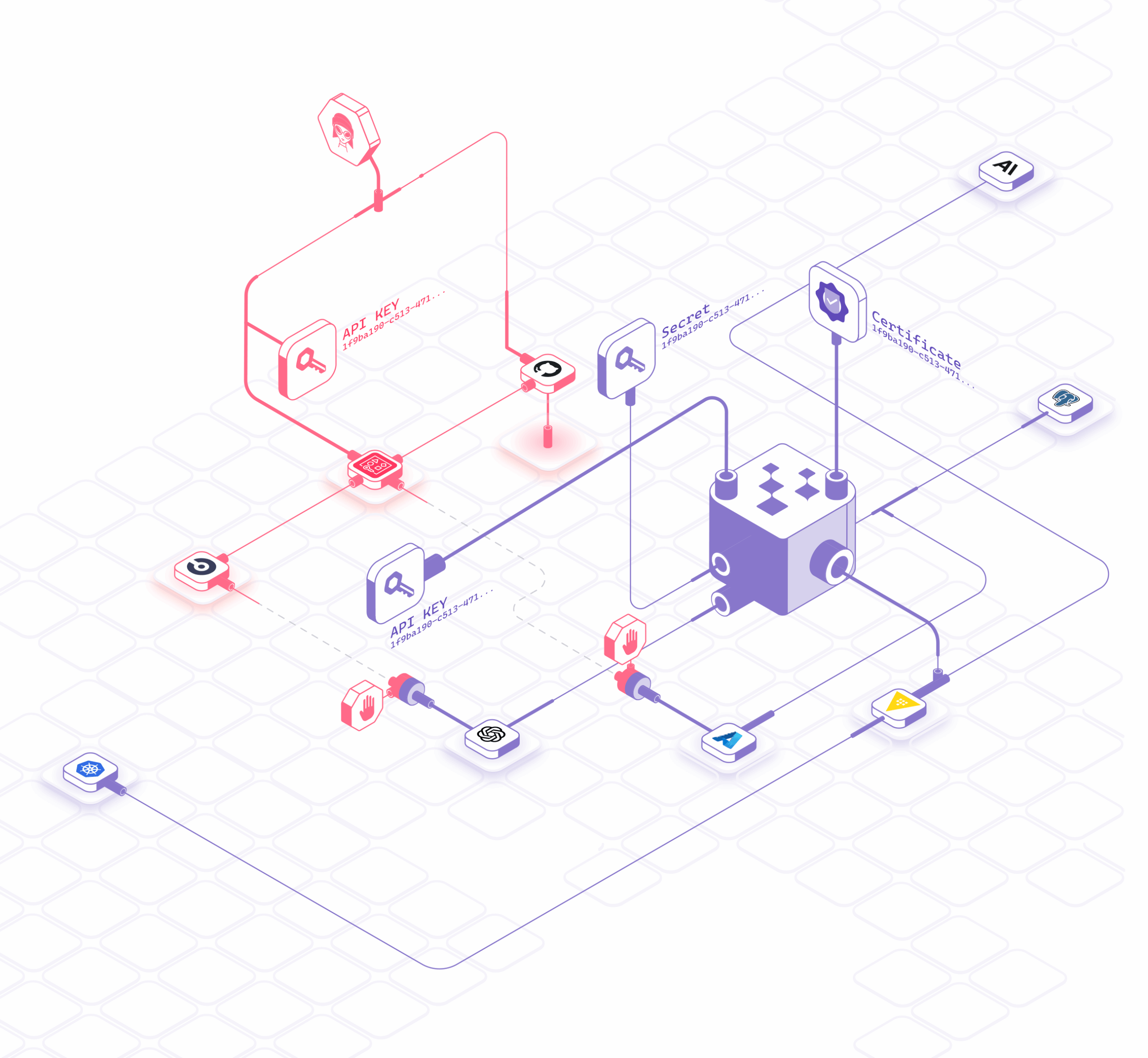
Replace Secrets with Identity-Based Access
No secrets means nothing to steal.
Hush Security’s patent-pending solution replaces secrets-based access with identity-based, policy-driven access for non-human identities (NHIs), so services and agents authenticate securely without leaving credentials behind.
The Challenge
Non-human identities keep multiplying: service accounts, workloads, CI/CD jobs, automation, and now AI agents. Most of them still rely on static secrets that are copied across systems, rarely rotated, and hard to track.
Even when teams invest months in cleanup, secrets creep back in through:
- New services and pipelines
- Vendor integrations and scripts
- Emergency fixes and hardcoded credentials
- AI agents, MCPs and autonomous workflows
The Solution
No more chasing leaked keys. No more brittle rotations. Just secure, controlled access at runtime.
Hush moves teams from distributing credentials to enforcing identity-based access across environments. Using the SPIFFE framework, we mint short-lived, just-in-time permissions for each machine-to-machine call and continuously validate and attest identity and context at runtime. You declare access policies, and Hush enforces them continuously.
Secretless Access Across the Enterprise
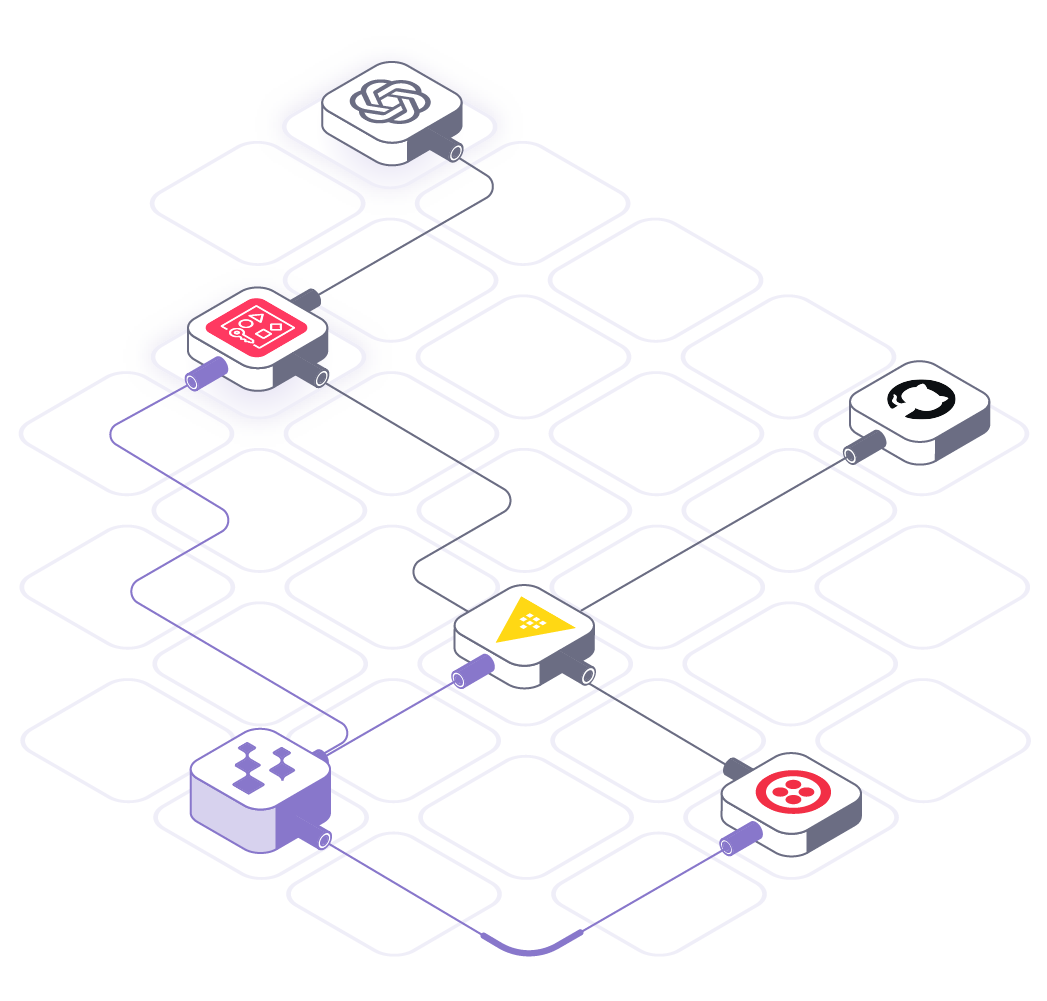
Replace static credentials for:
- Service accounts, workloads, and CI/CD automation
- Internal services and service-to-service access
- AI agents and autonomous tools
- Infrastructure and platform workflows

Identity-Based Access, Enforced at Runtime
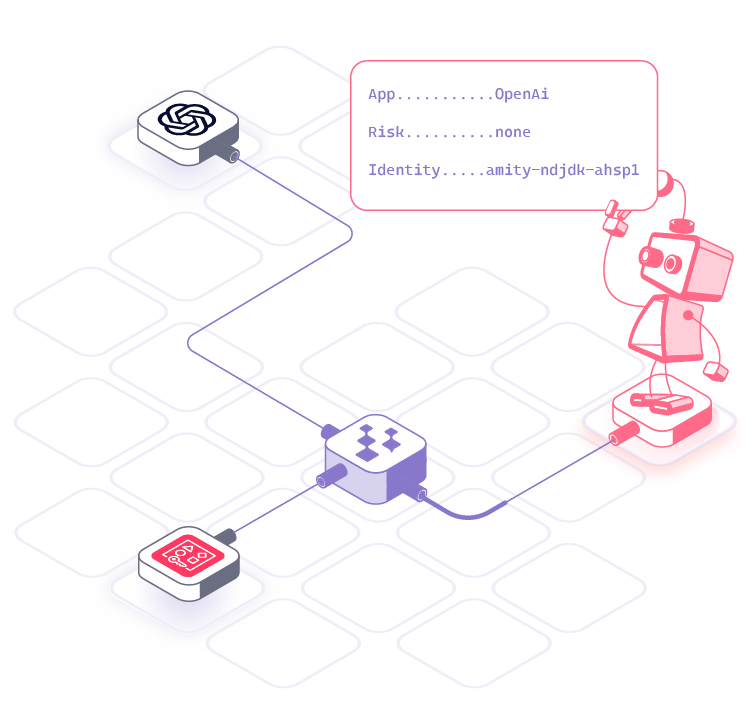
Access policies are automatically created and reviewed to enforce access based on:
- Access granted only when required, enforced in real time
- Least privilege by default, exact permissions for the exact time needed
- Continuous verification and attestation to prevent drift and misuse

The Value
 Risk Reduction
Dramatically reduce risk tied to stolen or leaked secrets
Risk Reduction
Dramatically reduce risk tied to stolen or leaked secrets
 Operational Efficiency
Reduce rotation toil and operational overhead
Operational Efficiency
Reduce rotation toil and operational overhead
 Attack Surface Reduction
Shrink the attack surface by removing long-lived credentials
Attack Surface Reduction
Shrink the attack surface by removing long-lived credentials
 Policy Enforcement
Enforce least privilege access with runtime context
Policy Enforcement
Enforce least privilege access with runtime context
 AI Agent Security
Enable secure AI agent rollout without uncontrolled credential sprawl
AI Agent Security
Enable secure AI agent rollout without uncontrolled credential sprawl
Moving to Secretless Access is Inevitable
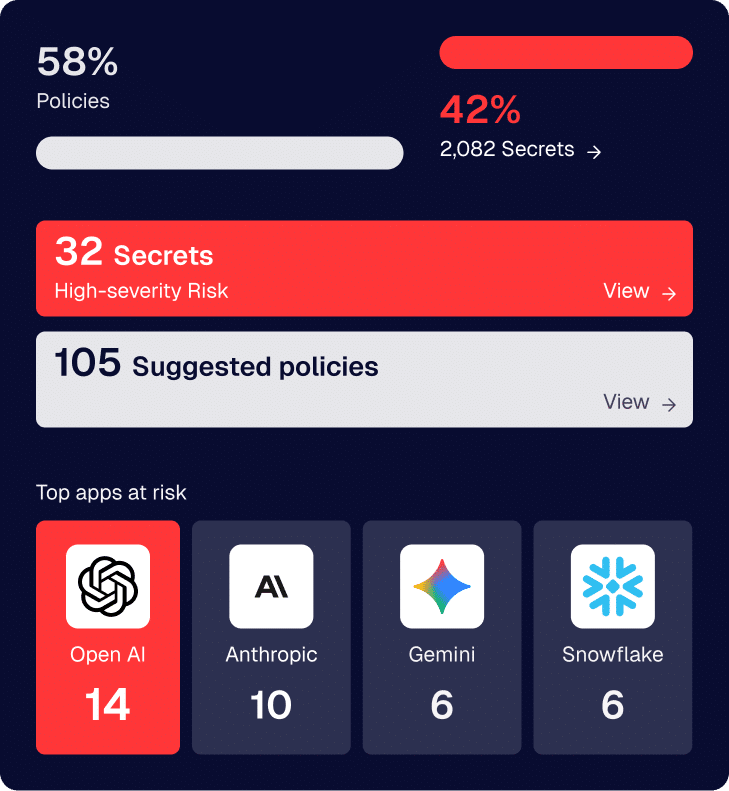
Credentials are the number one attack vector. API keys, tokens, and passwords leak, get reused, and give attackers persistent access.
At the same time, AI agents and modern cloud environments are exploding the number of machine identities and machine-to-machine requests. Managing static credentials across dynamic services simply doesn’t scale.
That’s why architectures are shifting to identity-based access for machines: no distributed secrets, just verified runtime identity and policy-based authorization on every request. Agentic AI is accelerating this shift by forcing organizations to treat non-human identities like first-class IAM principals, and the secrets-based model can’t keep up.