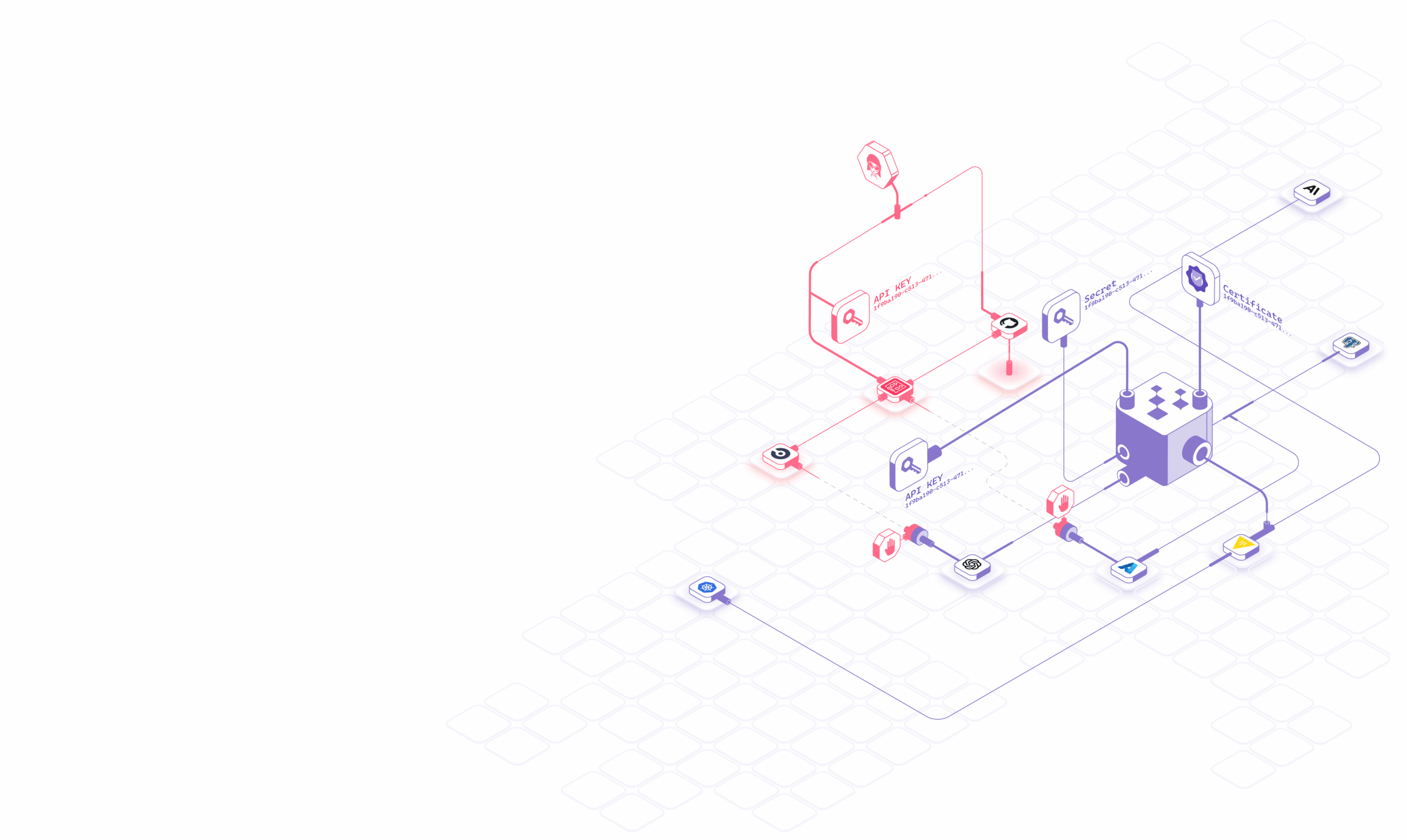
Secret Detection
Catch Secrets in Motion, Not Just in Repos.
Detect secrets exposure as it happens, understand real usage, and prioritize the risks that matter most based on live runtime signals.

The Challenge
Secrets don’t just live in code. They live in motion.
In modern environments, secrets move through CI/CD pipelines, ephemeral workloads, service-to-service calls, automation tools, AI agents, and third-party integrations. They get copied, forwarded, injected, logged, cached, and reused across environments, often without clear ownership or lifecycle control.
Traditional secret detection is mostly static. It scans repos or configurations and tells you what exists, but it can’t answer:
- Which secrets are actually being used right now?
- Traditional scanners find thousands of exposed secrets – but which ones are actually being used in production?
- Which exposures create real, exploitable risk today?
The Solution
Instead of point-in-time findings, get real-time detection, full context, and clear prioritization.
Hush Runtime Secret Detection combines continuous discovery with live runtime visibility to detect secrets where they matter most: during real execution.
We observe how secrets are accessed and used across live workloads and machine-to-machine activity, then correlate those signals with posture, ownership, and access paths to identify which secrets are actively risky, exposed, or misused.
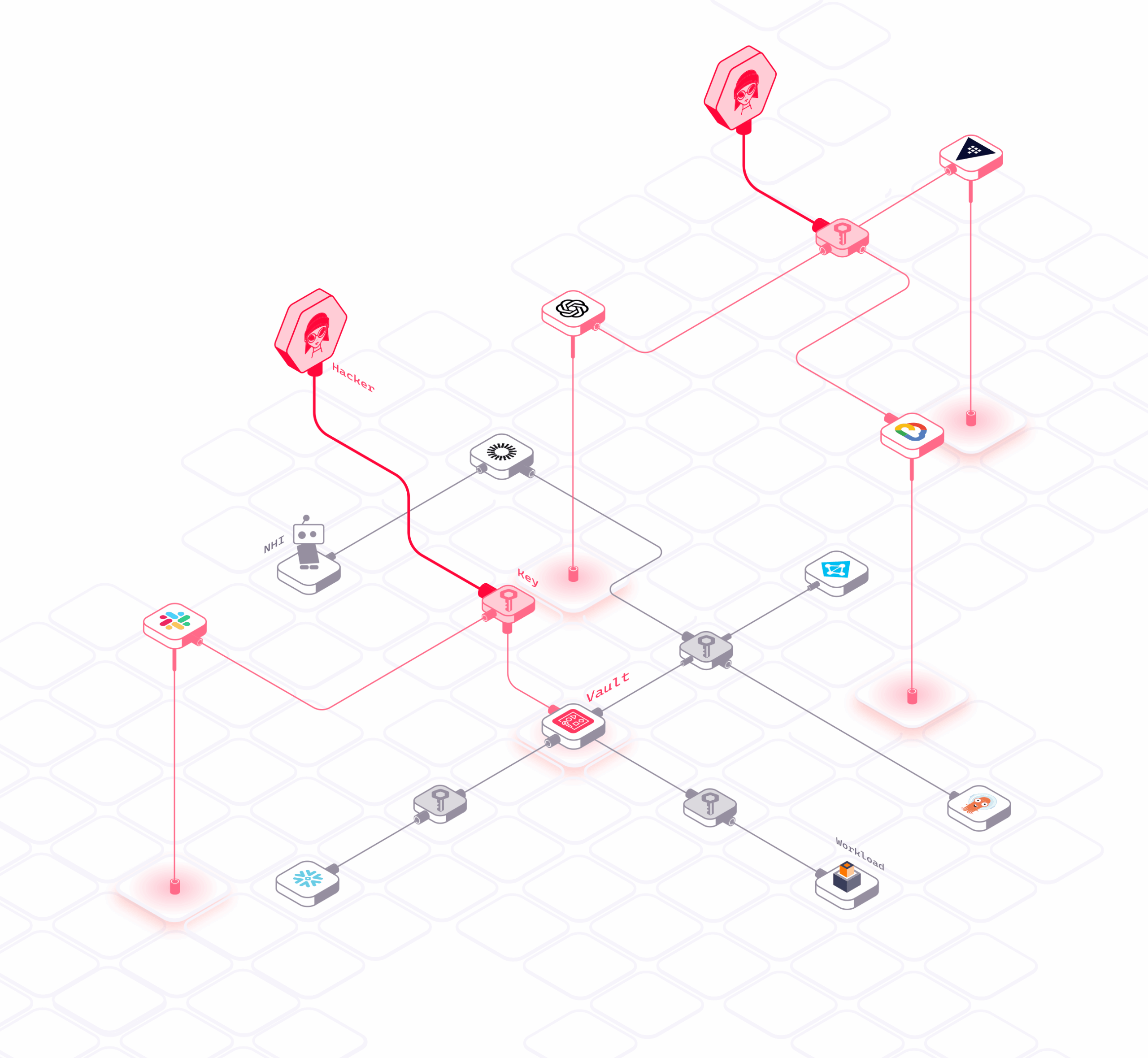
Runtime Secret Discovery
Automatically discover secrets across:
- Static + runtime detection to catch secrets in code, configs, and live execution
- Usage-based prioritization to focus on the most risky, actively used secrets
- Broad environment support across cloud, SaaS, on-prem, hybrid, and ephemeral workloads (including AI agents)

Full Context for Every Secret
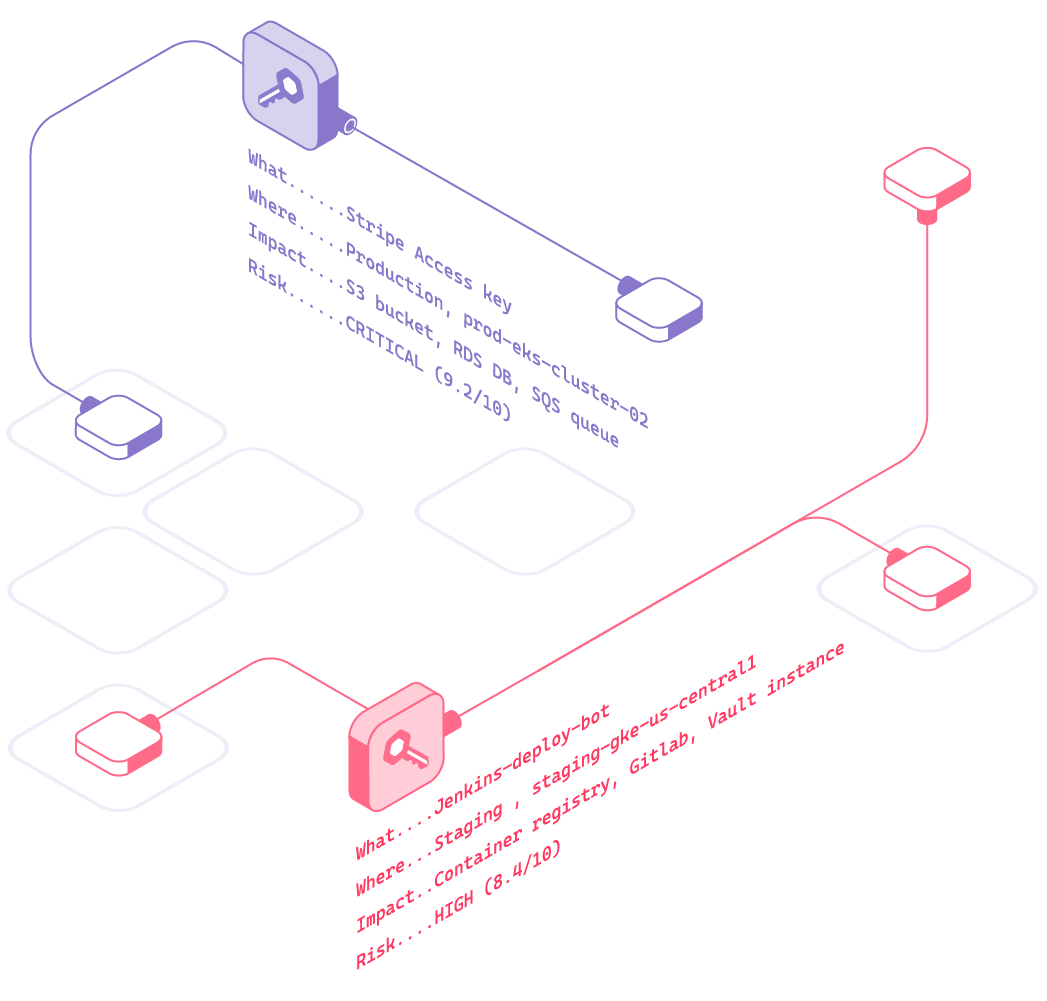
For every secret exposure or usage event, Hush provides the context teams need:
- What – workload identity, service, or agent
- Where – environment, namespace, and runtime conditions
- Impact – systems, services, and data
- Risk Level – based on posture and runtime behavior

The Value
 Runtime Detection
Detect secret exposure in real time, not after the fact
Runtime Detection
Detect secret exposure in real time, not after the fact
 Usage-Based Prioritization
Prioritize risk based on live usage and real blast radius
Usage-Based Prioritization
Prioritize risk based on live usage and real blast radius
 Noise Reduction
Reduce noise by focusing on secrets that are actually active
Noise Reduction
Reduce noise by focusing on secrets that are actually active
 Attack Surface Reduction
Shrink the attack surface by surfacing weak patterns and overuse
Attack Surface Reduction
Shrink the attack surface by surfacing weak patterns and overuse
 Fast Time to Value
Fast time to value with lightweight deployment and minimal integrations
Fast Time to Value
Fast time to value with lightweight deployment and minimal integrations